Resources/Tips
- Link to challenge
tl;dr
- Disassemble the program in IDA
- STAGE ONE: Skip the anti-debugger by not using a debugger
- STAGE TWO: Byte patch out a test that will always FAIL
- STAGE THREE: Enter in the flag (plaintext in disassembly)
- “Login” to the system
Walkthrough
Stage 
Just by running the program initially we get this: 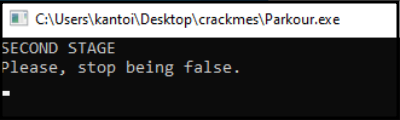
After disassembling the program the first thing that pops up is the anti-debugger check:
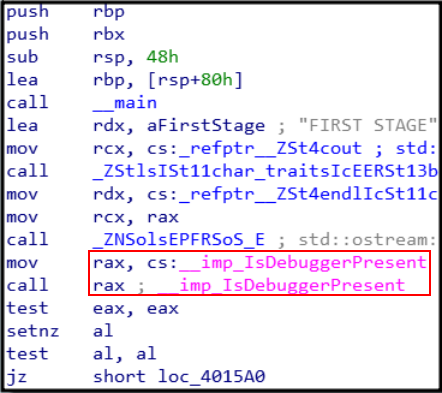
Which shows the following when run in a debugger: 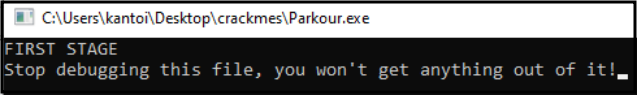
Stage 
The program has been coded in such a way that the jump to the early exit “Please stop being false” is always taken. 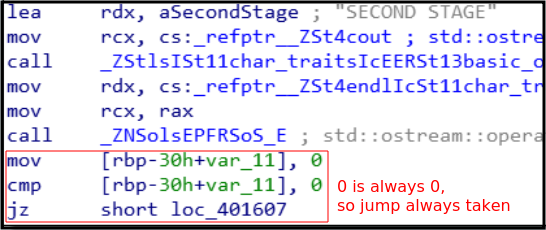
Therefore, to bypass this we need to make the comparison false, and the simplest way to do it is to change either one of the zeroes into a one!
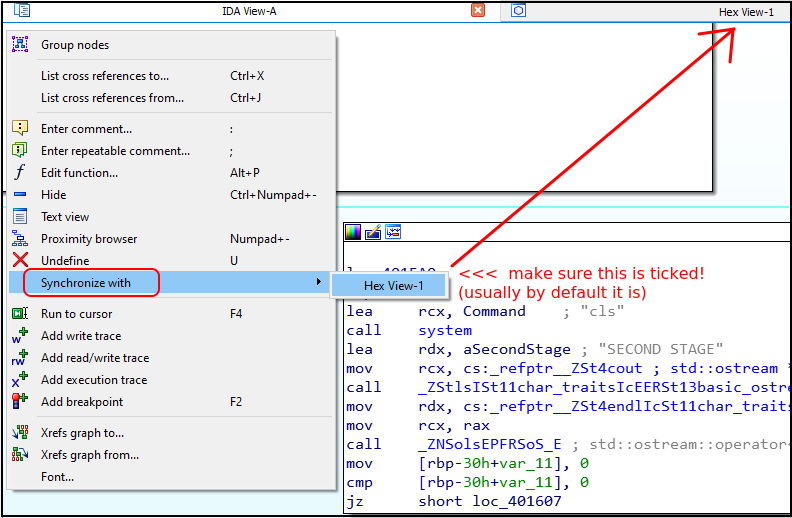
By switching over to the Hex View we can look at the actual machine code, and here is where we will patch the following area:
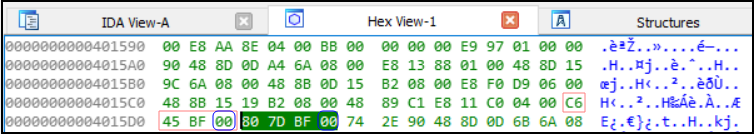
As shown above: mov(C6) and cmp(80) instructions present along with 00’s
To patch, simply do the following:
- Put the cursor infront of the byte you want to change
- Right click and “Edit”
- Replace the value you want, in this case
01 - Right click and “Apply changes”
(Note that F2 can be used as shortcut too)
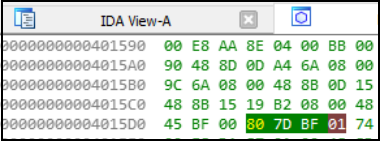
The binary should now be like this:
Finally, we should save as a new file: (recommend making a backup!) 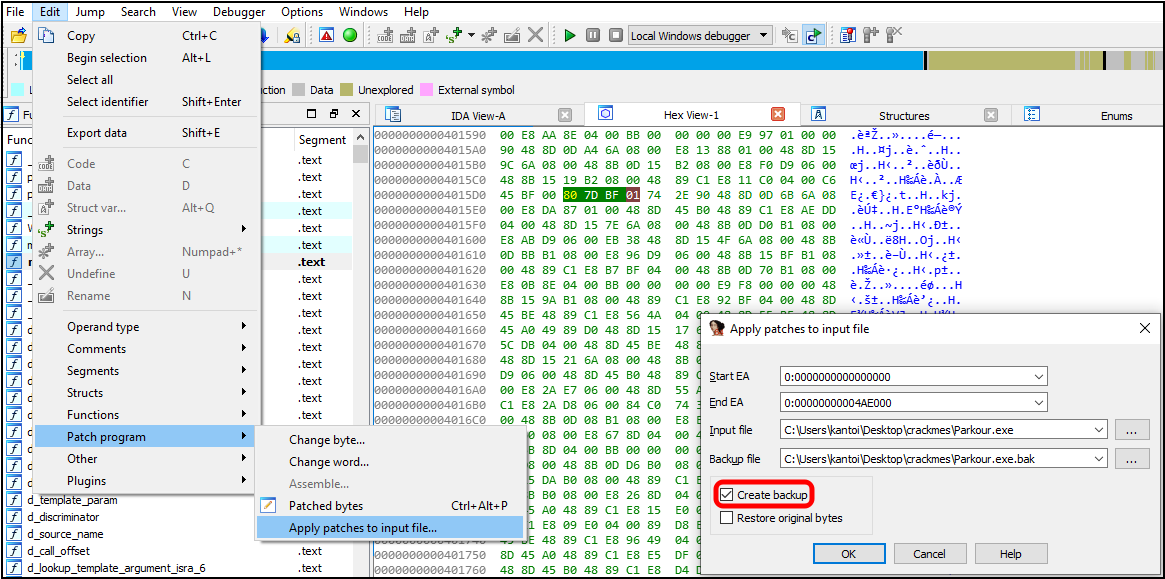
Stage 
When opening the new file, we are greeted with a new message mentioning the third stage!
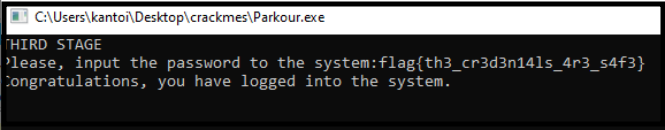
After entering the flag (which can be found in plaintext in the disassembly), we successfully log in to the system ![]()
What I learned
- how to use IDA to patch programs (backup the original!)
- learning how to draw connections between the pseudo-code IDA generates and what the program is actually doing