Resources/Tips
-
Link to all the Flareon’19 challenges

- Use
DNSpyfor this one — It’s good for disassembling C# to almost source! - Know how XOR encryption works!
tl;dr
-
A double-stage challenge:
- STAGE ONE: PLAINTEXT IN SOURCE!
- STAGE TWO: XOR DECRYPTION!

Walkthrough
Apparently C# decompiles to source in .NET, who would’ve thought? 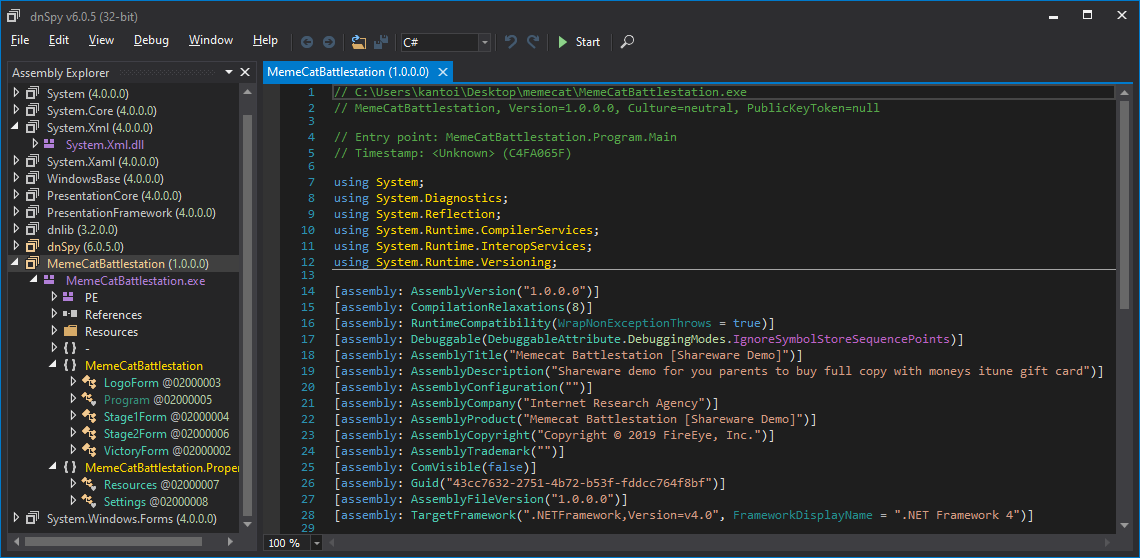
Looking at the main function we see the following: 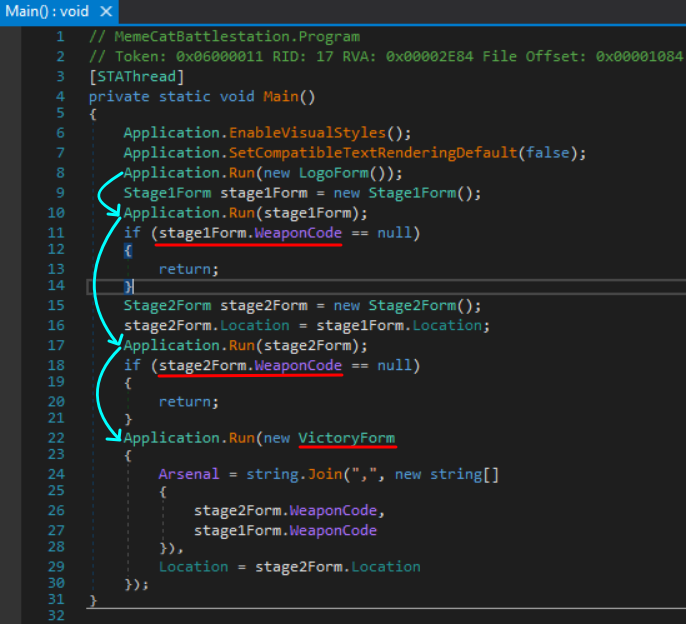
There are two stages to pass which then brings us to victory! Also the WeaponCode properties seem interesting, which warrants closer inspection…
Stage ![]()
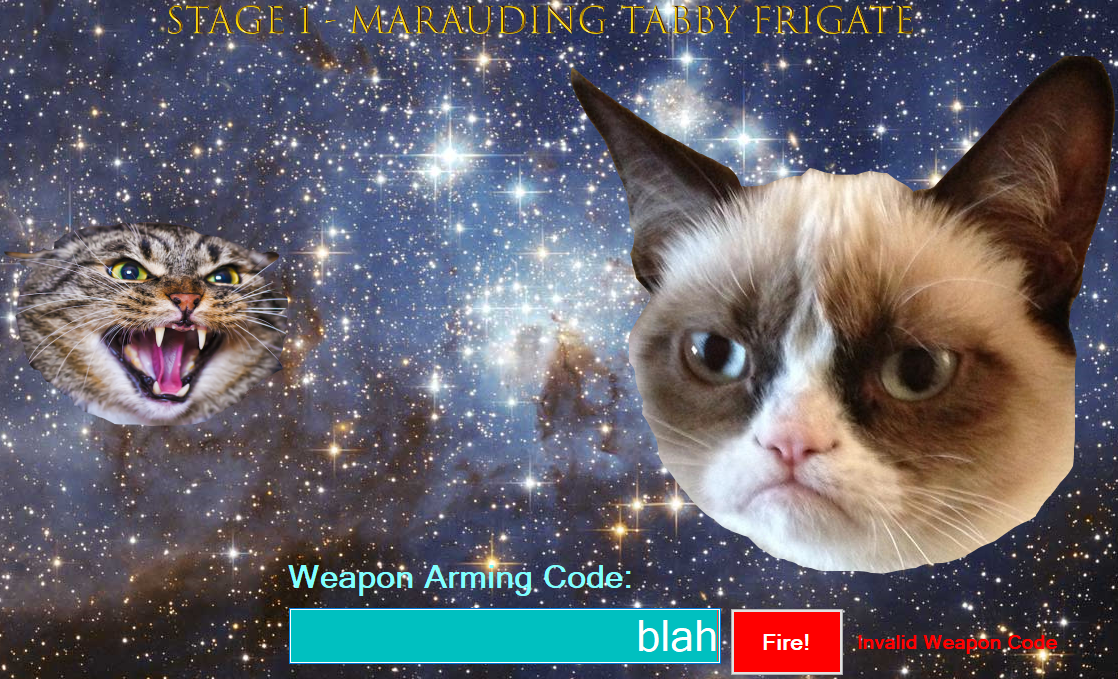
As we see from the screenshot above, entering the wrong code gives an “Invalid Weapon Code” message, lets see where this is invoked!
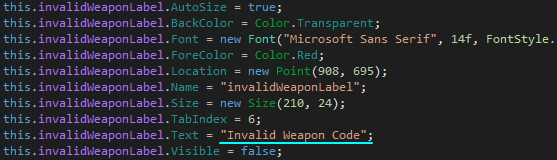
The string leads us to the stage1Form from earlier, and we discover the following function which referrences it:
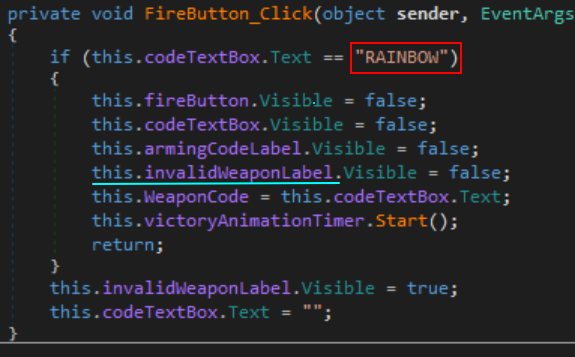
From here the plaintext string “RAINBOW” is identified to be the code for stage1 ! We enter it and watch the magic happen: ![]()
Stage ![]()
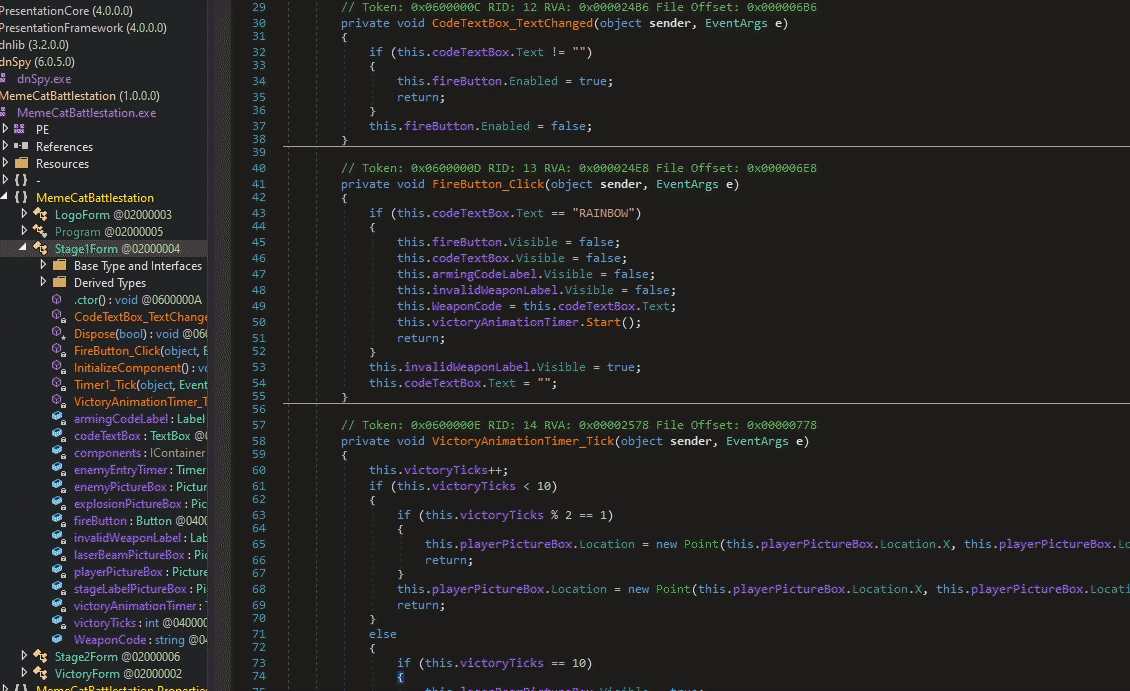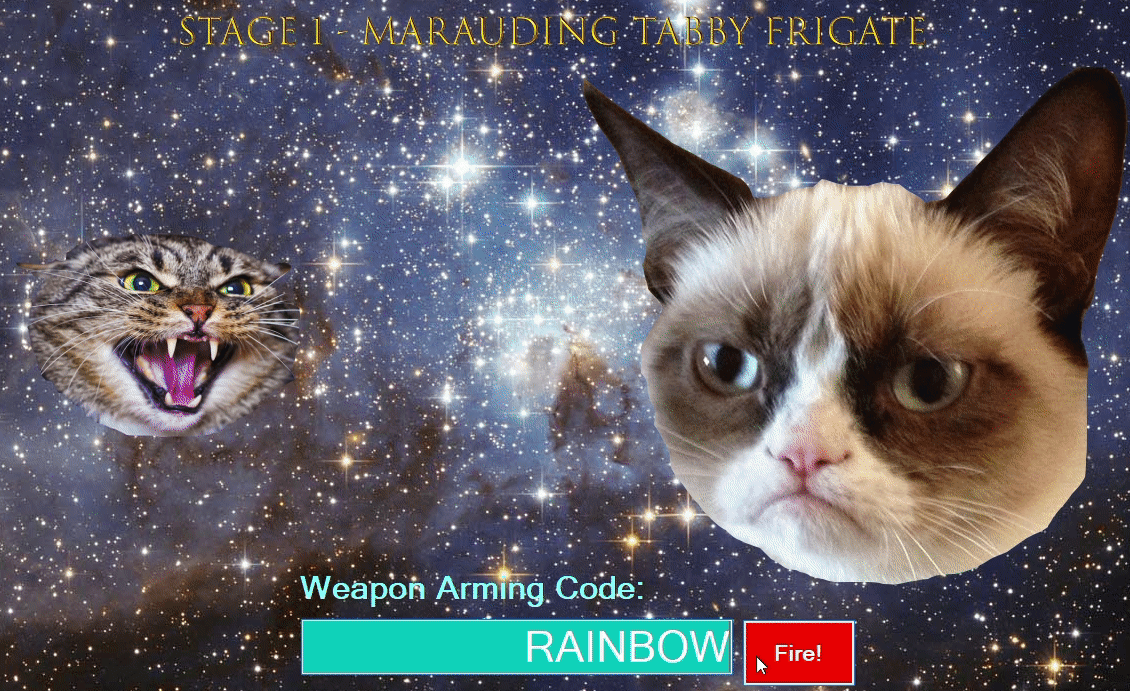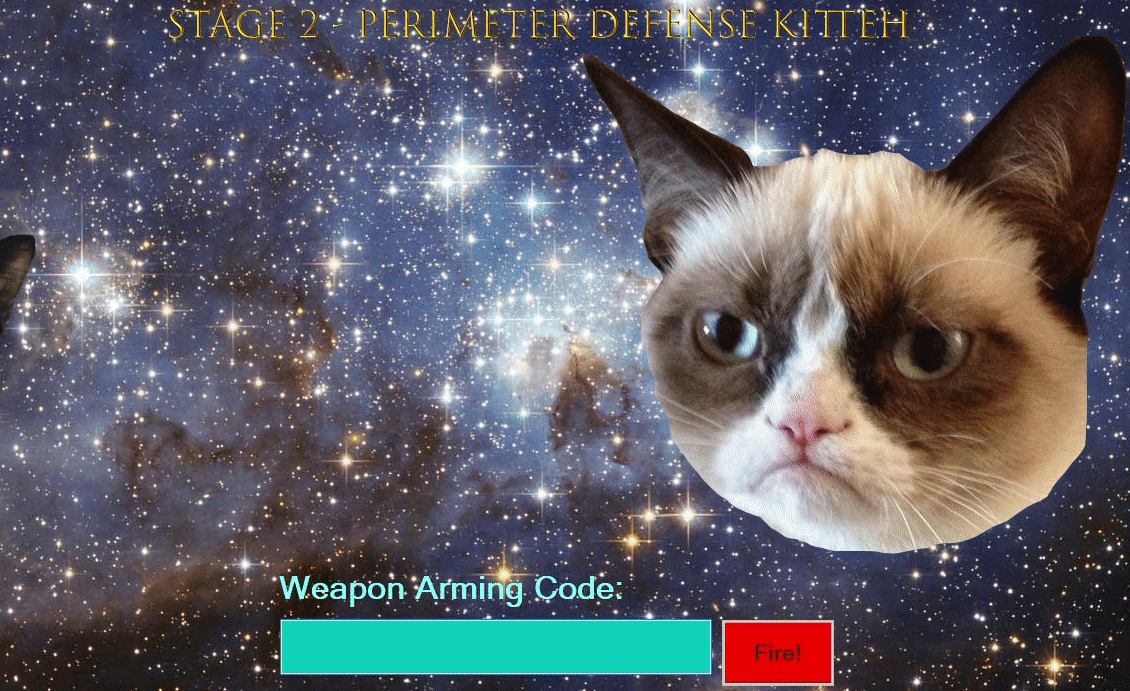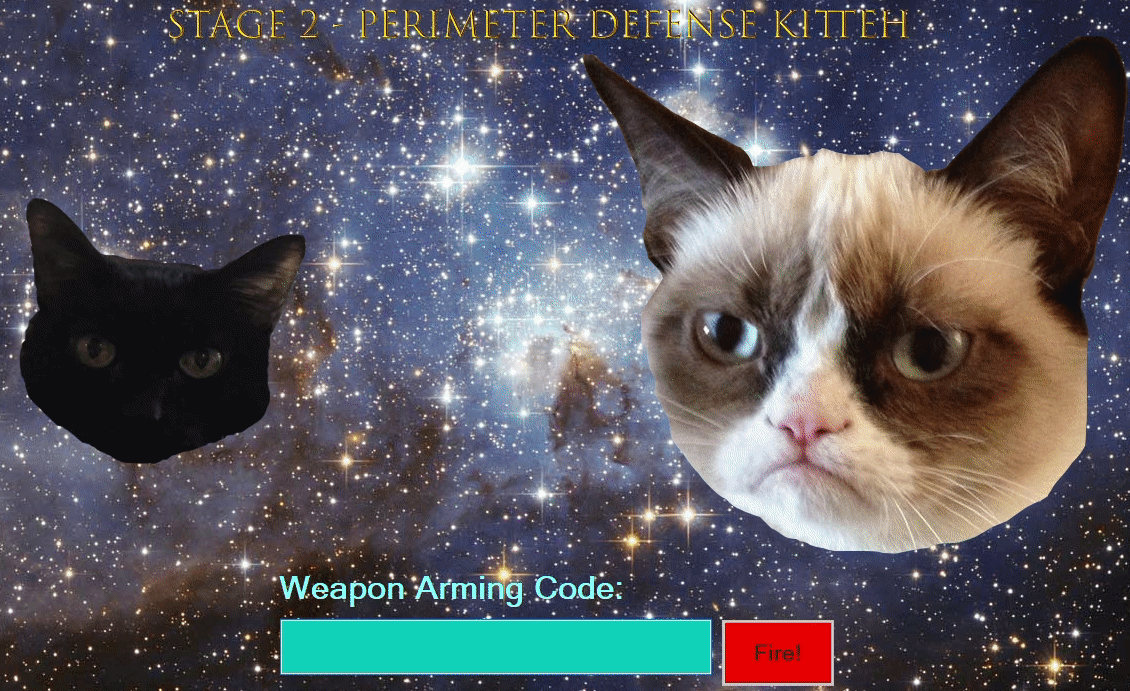
We know all that jazz so we skip straight to the FireButton_Click function in the stage2Form.
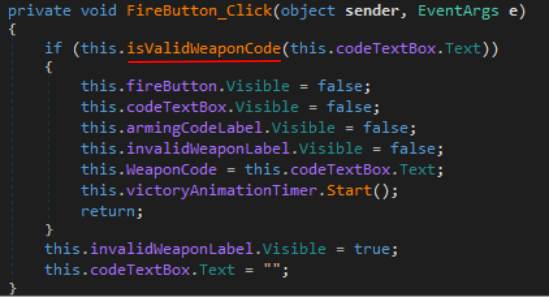
This time we see that the input string is being compared in a new function:
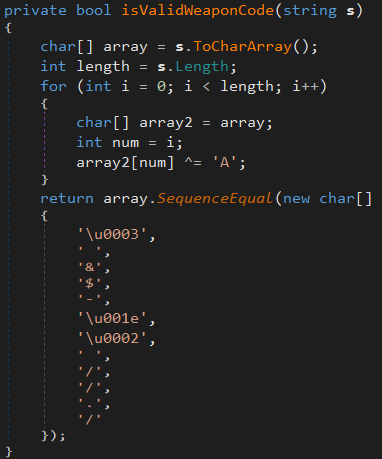
The function returns True if the input string XOR’ed with ‘A’ matches that random obfuscated string there…
After writing a simple Python script to solve, we get the code~
#!/usr/bin/python
obfus = ['\u0003',' ','&','$','-','\u001e','\u0002',' ','/','/','.','/']
original = []
for char in obfus:
dec = ord(char)
# Direct XOR'ing between characters not doable in Python
new_dec = dec ^ ord('A')
new_char = chr(new_dec)
original.append(new_char)
print("".join(original)) # ~~~~~~~~~~~~~~~~~> Bagel_Cannon
After entering the code and watching the cool animation we get the flag!

What I learned
- How to use
DNSpy - The rough layout of C# programs and how they are packaged