TL;DR
I wrote this just to shed some light on what malicious operations are out there, what thought processes this actor was having, and the tactics/technologies being employed by both sides in attacking/countering. After all security is a somewhat cat-and-mouse scenario ![]()
![]()
So… what happened?
Well my friend on Facebook executed some dodgy Javascript that they shouldn’t have — triggering a CSRF on Facebook/Messenger to spam his friends list (including me) with a very interesting message:
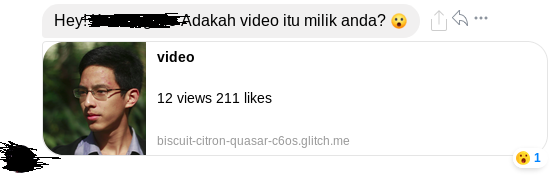
Loose translation: Hey! Is this your video?
Some interesting observations:
- The script was able to detect his Facebook language settings
- It would mimic the language for the most effect
(compared to just sticking to English)- Clearly their target(s) are not restricted to any country.
- Its a drag-net style phish, aiming to hit anyone and anything

- The downside to this is if you get the language wrong, it raises suspicion and kills the phish attempt altogether…
- It would mimic the language for the most effect
- The message was also tailored with the profile picture of the victim
- Really nice touch to make it more personal
- Social engineering at play, enticing victims to click
- It really targets people’s insecurities
- we Sec people tend to forget, not everyone is good at OpSec

- we Sec people tend to forget, not everyone is good at OpSec
Sandboxing time
Here’s the URL in question:
https://biscuit-citron-quasar-c6os.glitch.me/#J3wAVJ6IIYF7YG30W4SVxko7Jj6ze%2Fm4lwcHO00oY7Oh1fg4YjHN%2B9Lb9sUEq3T2UoUwpf30WxbdG1C8ys1nyv%2B0hWzGF9ua%2B6baC9x0QkuZpton6sa1kXT17hZKyAAv%2Fqe1UeL0d8URKFd8J8R4tZCOMYbAy%2FhXq9af47CQ2bLIEdNGqFwe%2BZNKT0Mw8KtfdV5lBKRCkXWtVD6bjFVvNeWSYYGGP3RuFGrBfiwzYKkcnPPjvjD7Crz7yMpgJEIZbA4IAJCK%2BpfbtwCnXB2i6WnoBynw%2FA4xYhm5ue8%2Fob5Zas3rWxJuTOE0pvu1Xa17O4HlNCjJoTFnm8bMTYO%2FOA%3D%3D
Not wanting to risk executing any Javascript locally, and also not wanting to spin up a VM – I visited the link with browserling
Jekyll and Hyde
Unfortunately at the time of writing I wasn’t able to retrieve the source, and I didn’t save it before the malicious app got removed
The Platform
Did some digging around the URL and discovered that the app was being served on a legitimate platform known as Glitch
It’s a less technical version of GitHub as far as I can tell, it promotes code-sharing and collaboration, but edits are similar to spreadsheets and not commit-based.
The main point here though is that no accounts are needed to store and host code. The malicious actor created multiple instances of their app without needing to leave any information behind. ![]()
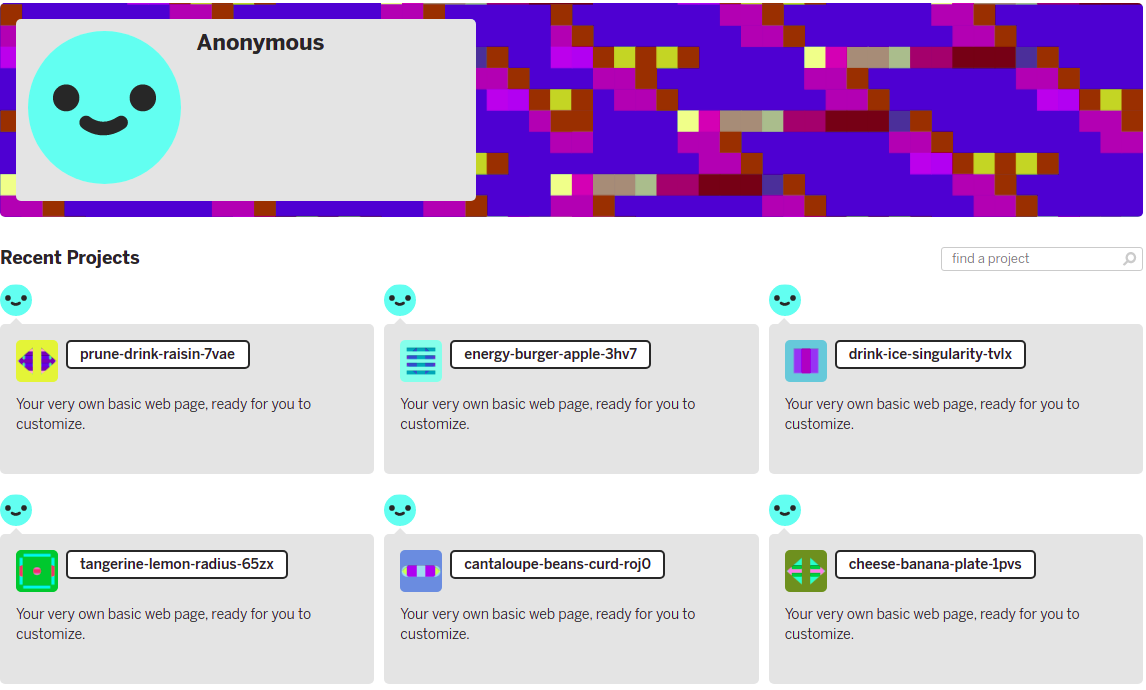
The App
The harmless app that loads initially is a weather forecast widget on a grey backround. Thats about it…
The Hidden JavaScript
The hidden JS is either obfuscated or pulled in from a remote server. Without doing any reversing or fully reading the code, it:
- Checks what browser version you’re using
- With Sandbox using IE, it doesnt do anything malicious
- With Firefox and Chrome versions ~65 or over, it does dodgy stuff
- Sends a POST request with a token to
weatherapi.pro
(I think its the same one as the commented section in the URL)- Users not knowledgable about domains/TLDs might not see the issue
- But most of us would be slightly aware of
.prowouldn’t we?
- Makes additional requests to:
xxx.dtscout.comxxx.eyeota.com- These are seemingly used for analytics
- They are actually tracking how many and where people clicked from!
- Perhaps to log IPs for future attacks?
- After all they do not have access to the logs on Glitch
- Finally — serves up a generic phishing page
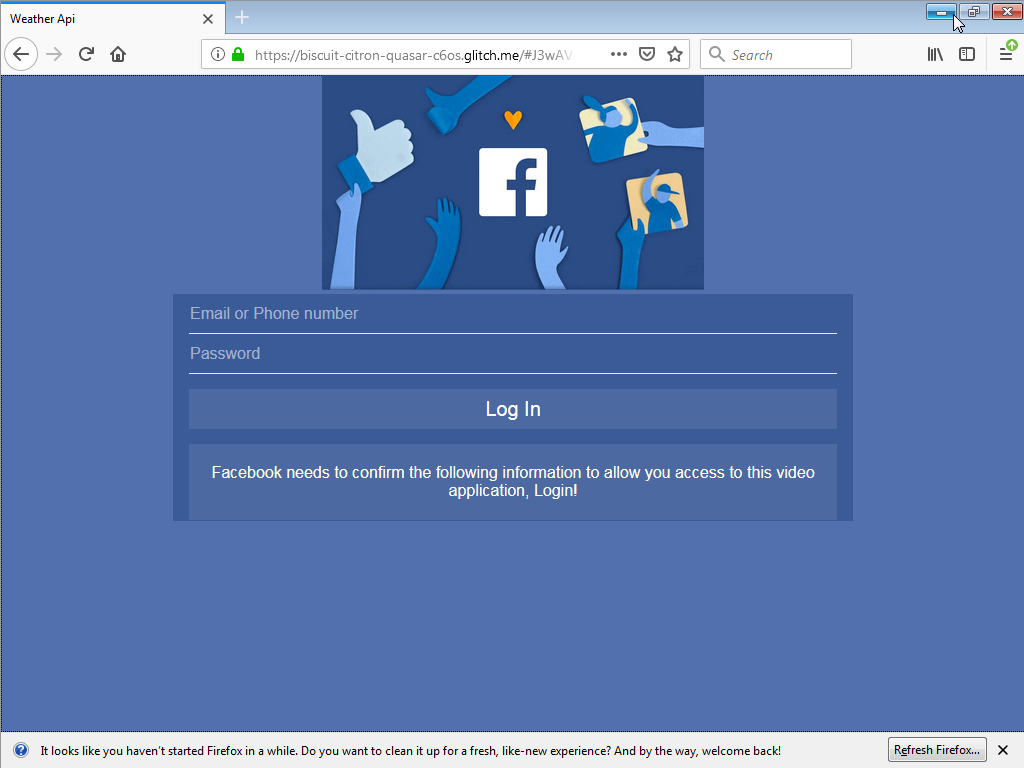
The control server
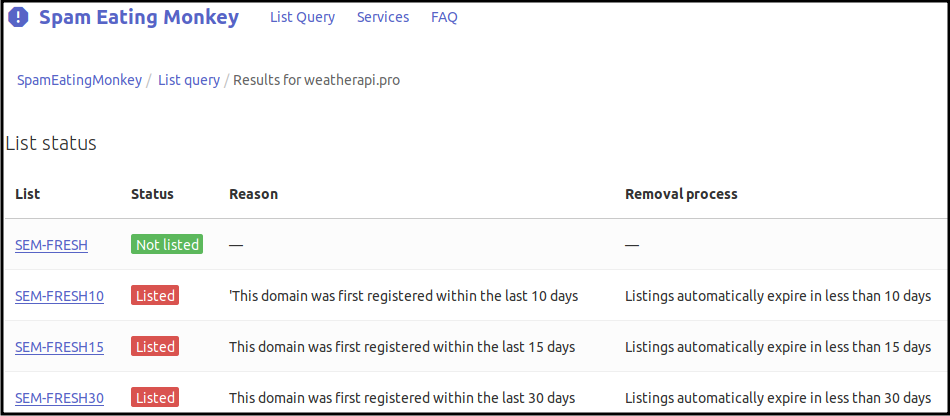
Using whois it shows that weatherapi.pro is served by
NS-CLOUD-E*.GOOGLEDOMAINS.COM… probably a Google Cloud Compute instance?
The domain registrar is NameCheap, the domain itself was purchased just 6 days before the trap was activated ![]()
When visiting, a simple GET request only returns {"status":"200"}, which might fool most people, but I believe they’re relying on some obscure system of tokens and passwords in the backend to determine what content to return or to “play dead”.
Update: 8th June
So I checked back today and guess what? 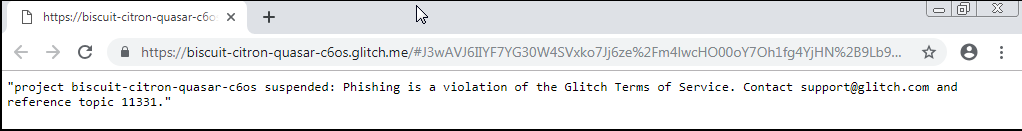
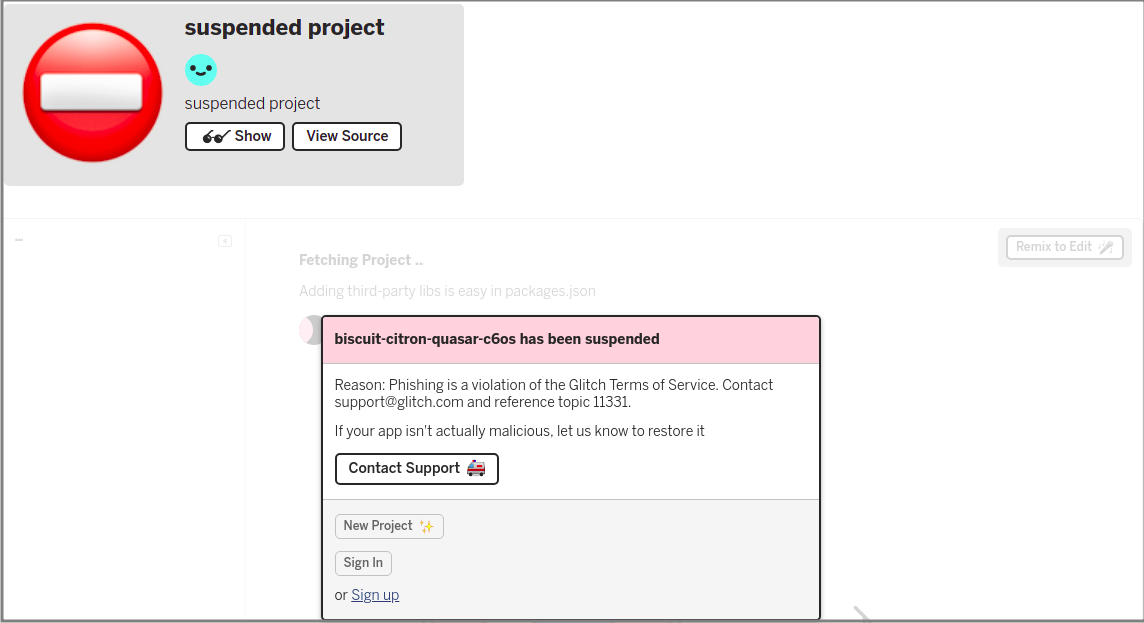
Kudos to the Glitch people for quickly responding to either an internal check or user reports ![]()
The webserver at weatherapi.pro was also taken offline, the malicious actor is probably cleaning up their tracks or having their resources terminated by Google ![]()
Final words
I approached with caution initially because I thought it was a server that
- delivered drive-by downloads for malware
- served more malicious JS
In the end it was simply a complex but somewhat effective phishing setup.
To make it better they could have also customized the phishing page to follow the language settings of the victim, consistency is key for convincing victims that your page is legit ![]()
I found it interesting that they bothered to engage with analytics in their attacks as well, although I’ve been told countless times that attackers can be as professional as well-oiled developer teams as well ![]()
It’s sad for me to say this but I know people who are quite likely to fall for this, although it’s glaringly obvious for Sec people…