Foreword 
I was lucky enough to test an app that did not have the following headache inducing features:
- Certificate Pinning
- Anti-Debugging checks
- Root/Jailbreak Detection
- Code Obfuscation
The phone I tested on was a Pixel 2, which had the following characteristics:
- A/B Partitions
- Systemless root
I could have done it in an Android Studio emulator as well, but to get the full experience its best to use a real phone :)))
Here’s my experience and what I did!
I took 3 days to setup and 4 days testing/practicing methodology…
Setup
I first started by searching up guides on the Internet, and this blog post will most likely contain the same shit you see everywhere else – sorry in advance!
Pre-Rooting 
- Download the Android SDK Platform-Tools for access to
fastbootandadb - Download the Pixel2 Firmware here (I used walleye 200705, use whatever)
- On the phone, open up Settings->About Phone->tap on Build Number 7 times
- Now Developer Options should be enabled!

- Now Developer Options should be enabled!
- Go to Settings->System->(Expand Advanced)->Developer Options
- enable OEM Unlock (for flashing)
- enable USB Debugging
- The device should now show up in
adb devices- You might have to press ‘Allow’ on a popup on your device
Rooting pt.1 
- After searching through many tutorials, the only way to root the Pixel 2 is through systemless methods, and
Magiskis widely used for this~ - Simply download the
Magiskapk file through the device PlayStore- Or you can download it to your machine first
- Then sideload it using
adb install magisk.apk
For debugging at any time we can run
adb shellto drop into the system Notice that at this stage we are unable tosujust yet
- Then push the original boot image file onto the device:
unzip walleye.zip; cd walleye/; ls walleye-again.zipunzip walleye-again.zip; cd walleye-again/; ls boot.imgadb push boot.img /sdcard/Download/Magisk Manager -> [Magisk is not installed] -> INSTALL
- From there, use
Magiskapp to patch the original firmware file
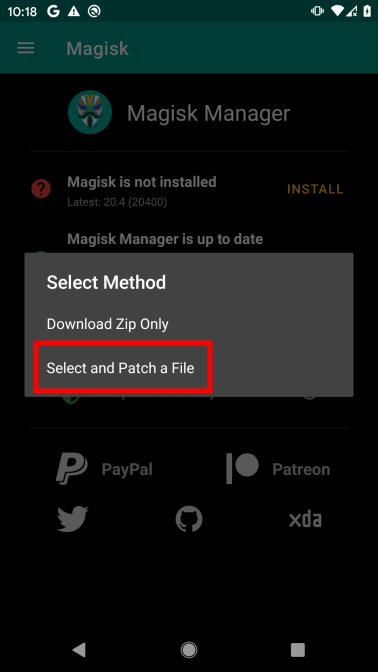
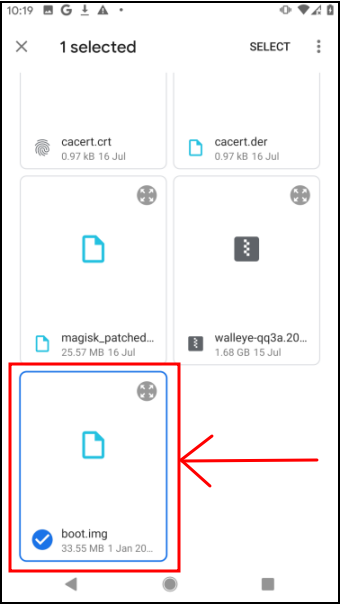
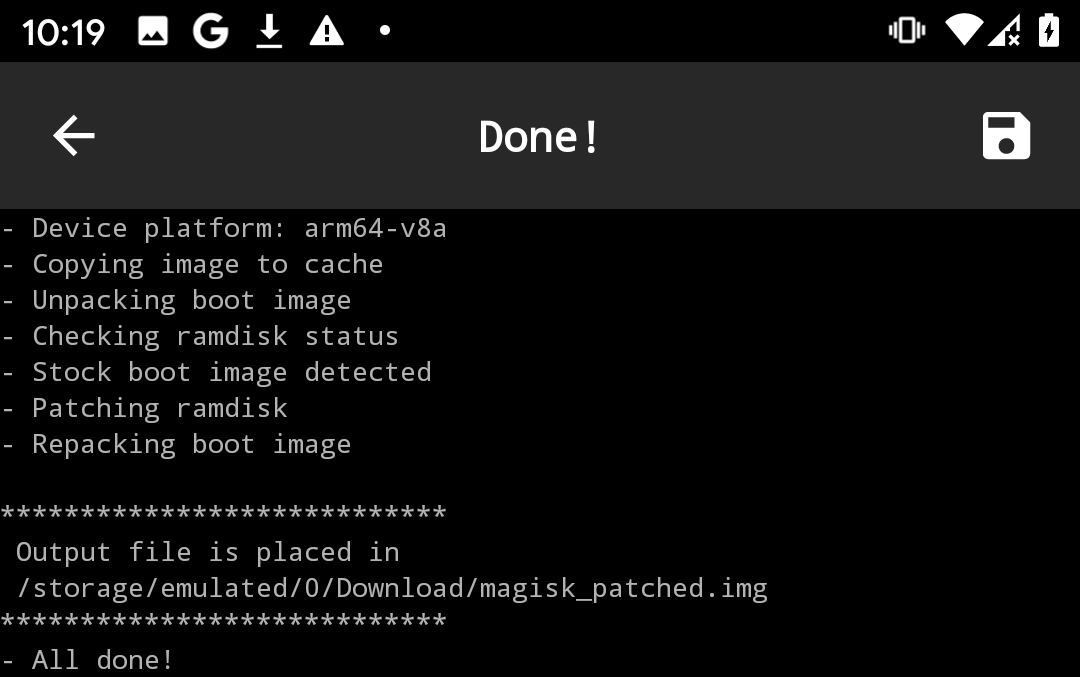
- Save the patched file to local device:
adb pull /sdcard/Download/magisk_patched.img
Reflashing 
- Reboot into the bootloader using :
adb reload bootloader - Unlock bootloader with:
fastboot flashing unlock - Flash the patched boot image:
fastboot flash boot magisk_patched.img - Relock bootloader if you’re nice
 :
: fastboot flashing lock - Rebooting time:
fastboot reboot
Rooting pt.2 
- You actually have to go into Magisk and go to hamburger and turn on superuser access

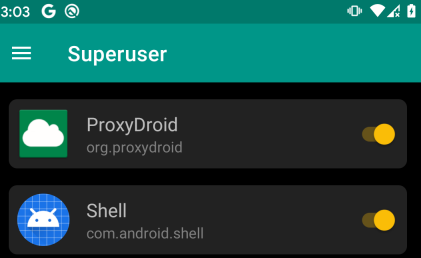
this is where I fucked up lol, don’t forget this step!
After this you should be able tosuafter entering theadb shell
-
Also a good tip is to install the Magisk Hide module which will repackage Magisk with a different name to evade Rooting Detection.
- From here you can run a SafetyNet check to see if the device is rooted AND undetected, if you don’t have two ticks you might be rooted but detected.
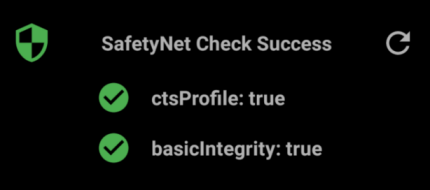
Installing stuff 
- objection
-
pip3 install --user objection(May be wise to setup virtualenv too)
-
- Drozer & Drozer Agent
- The Drozer Agent to be pushed to device, and turned on within the app
- Embedded Server:
[ON] - Port forwarding also needs to be done:
adb forward tcp:31415 tcp:31415 drozer console connect
- Embedded Server:
- The Drozer Agent to be pushed to device, and turned on within the app
- Frida
- The server component to be pushed to device and run in the background
adb push frida-server /data/local/tmp/ adb shell "chmod 755 /data/local/tmp/frida-server" adb shell "/data/local/tmp/frida-server &" # run as root pls - Check by running
frida-ps -U
- The server component to be pushed to device and run in the background
- ProxyDroid
-
Download and then sideload with
adb
-
Download and then sideload with
Tools
Mobile Security Framework (MobSF) 
- I usually install this as a Docker container for easy install + uninstall
-
docker run --rm -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest - Drag and drop the
.apkfile and let it do static analysis - Areas of note are:
- Receivers
- Broadcasters
- Activities
- Strings section
- anything interesting etc.
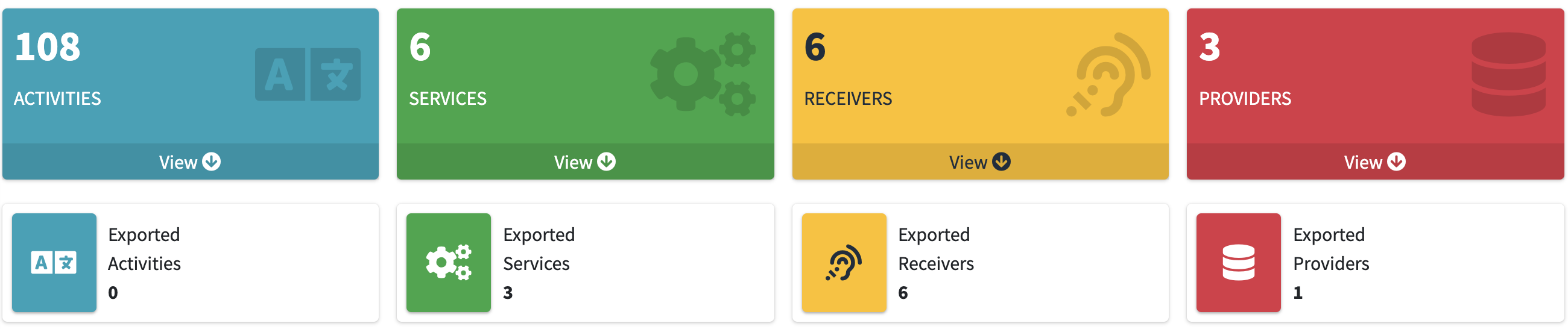
Useful for finding any low-hanging fruit at the start ![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Burp Suite  + ProxyDroid
+ ProxyDroid 
Don’t forget to install your BurpSuite cacert.der onto the device!
Had some trouble proxying traffic in the beginning…
- Proxying through the Android OS Wi-Fi menu works for web browsing —
but not for apps:
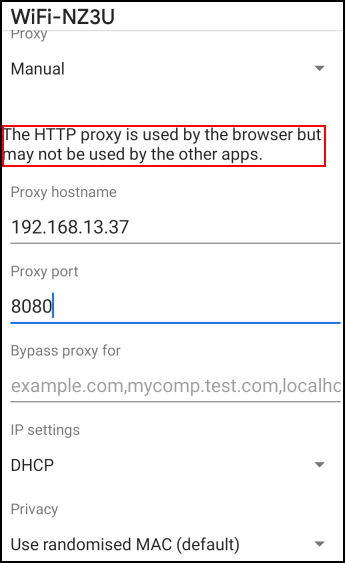
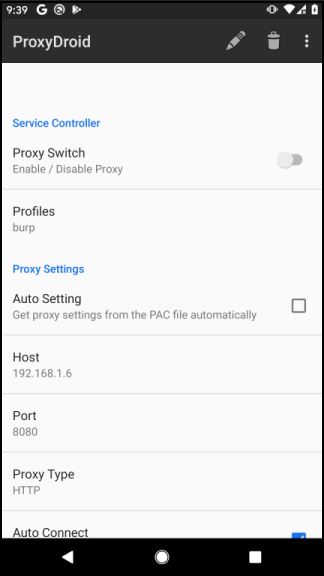
-
ProxyDroidsolves that problem as it can perform global/app-specific proxying (runs as superuser!)- The following settings should be used:
- ProxyType: HTTP
- Global Proxy (or Individual Proxy/App if you’re feeling confident)
- The following settings should be used:
jadx-gui 
- An
.apkis actually just a zip file containing more files in it! -
jadxallows us to decompile the APK and view (hopefully) the source - Other alternatives:
dex2jarandjar2dex,apktool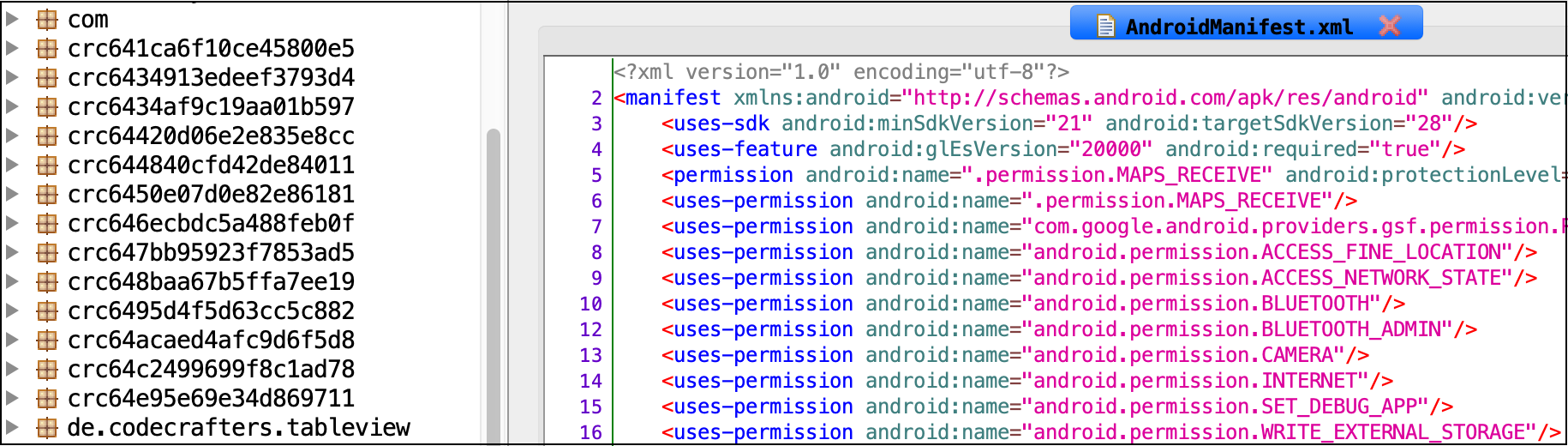
Frida + Objection 

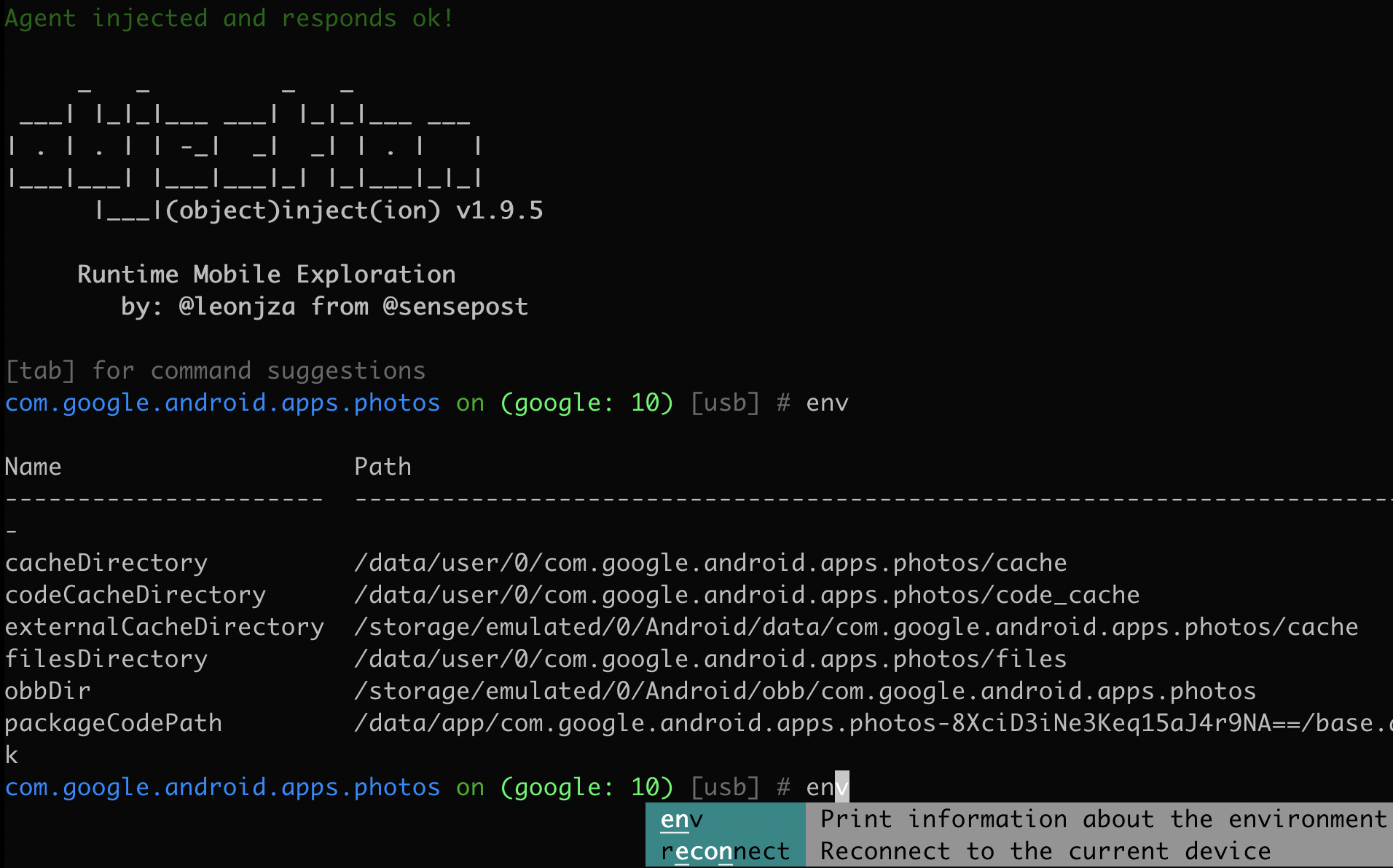
- Used for dynamic instrumentation, think manipulating runtime environment rather than changing code and repacking
- Objection allows for peeking into application memory, perhaps for cached data/credentials?
- Run with
objection --gadget "com.android.blah" explore
- Run with
drozer 

- Acts as a fellow malicious app on the device to see if it can intrude through exposed receivers/broadcasters
apksigner 
- Simple check to see if the packaging/signing is done properly, making sure no important files can be tampered…
apksigner verify --verbose app.apk
Methodology
I can’t remember all of it but the ones that stick out the most to me are:
- Use
adb logcatwhile using application/idle to look for debugging/error info that may be useful - Check for insecure files that have too wide cross-application permissions
- Check for Insecure Password Transmissions to the backend server
- Check for Insecure Exposed receivers/broadcaster/content providers etc
-
Check for bypasses to cert pinning, anti-debugging, anti-rooting
-
and of course you have the usual web application vulnerabilities too!
Reflections
- Apparently the Mobile Application Hacker’s Handbook is pretty useful!
- Didn’t get a chance to use it during my engagement, perhaps in the future!
- A good standin:
Mobile Security Gitbook
- A good standin:
- I’m not sure if I am prepared for the monster that is iOS testing… :trollface: