Disclaimer
This isn’t meant to be a full methodology, just a record of my experiences that day!
Background
So I got assigned to shadow another of my seniors (who shall not be named)![]()
The WiFi networks in scope were the:
- Guest wifi
- Corporate Wifi
Set up
1) We used the ALFA-AWUS036ACH wifi adapter:
- I actually have a TP-Link lying around at home that I can use, I will try it next time in my own time


2) The next step was to ensure the USB is mounted to a Kali Linux VM:
- Running
lsusbshould show the adapter in the list of USB devices
3) From there, we ran into issues with installing the necessary drivers:
- The package installation
apt install realtek-rtl88xxau-dkmsdid nothing. - This is why you shouldn’t always trust those random magazine-style guides on the internet

4) The way we got it to work was to follow this guide:
- Note the Notes and Installation section!
5) Finally, we check that the adapter is working with sudo iwconfig
6) From there its as easy as running hostapd-wpe
- in the config file you change the SSID to match that of the target ESSID
Wait how does it work?
The closer you are to the rogue base station the more likely you will auto-connect to it based on your clients’ familiarity with the known eSSID.
If its such a risk then why save eSSID?
Becase when you move throughout the building with multiple base stations, they act as repeaters of the network so you are always connected!
In theory at least. until one tries to fuck you over :)
Recon
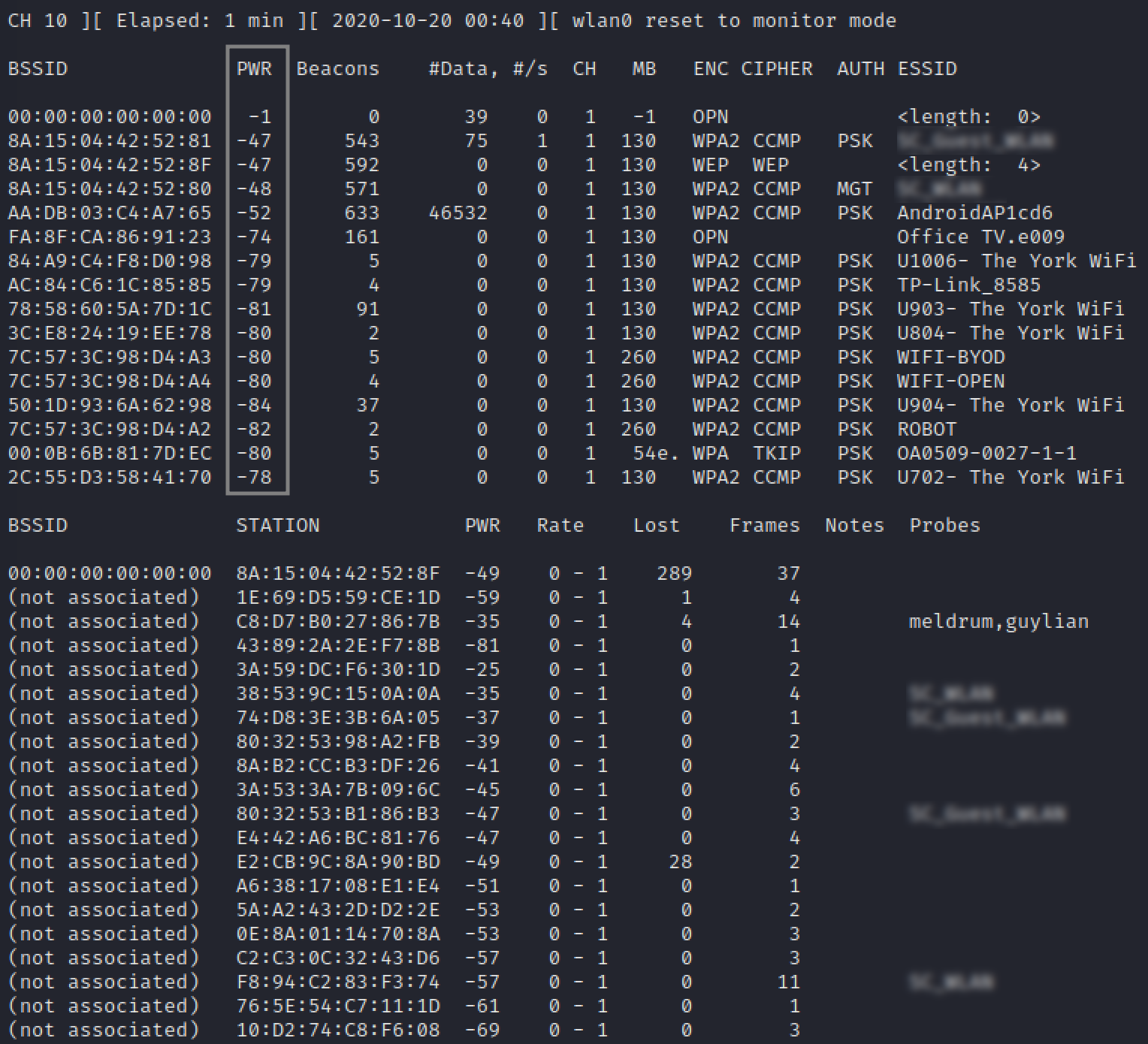
The tool used here is airmon;
- to monitor the network for probes and nearby base stations
- The probes can reveal where someone has been ie:
- Your mobile phone will be searching for previously connecteed Free WiFi such as MacDonalds
 etc…
etc…
- Your mobile phone will be searching for previously connecteed Free WiFi such as MacDonalds
- The probes can reveal where someone has been ie:
- These base stations are ordered by signal strength
- the lower the negative number (closer to the top), the closer it is to us
Rogue AP / Evil Twin
The corporate WiFi uses untrusted/unverified certificates:
- This works in our favour as users are more likely to accept the fake certificates presented by the rogue AP
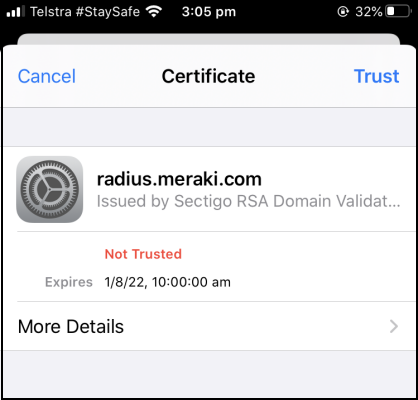
We use apd_launchpad to:
- generate a fake certificate
- stick the fake certificate and fake eSSID into a
hostapd-wpeconfig file
Then we re-launch hostapd-wpe which will display a visually similar error and certificate name
Now we wait
At this point it is a waiting man’s game.
We have to wait for users devices to send auto-cached credentials…
However in this case because of the existence of certificates, user interaction is ![]() % required.
% required.
They have to click Accept before the authentication prompt pops up!
Deauth Attacks
We decided to use a more active approach when still no results came in.
The aireplay-ng tool can be used to send crafted beacon frames to chosen APs in the vicinity.
The idea is to send deauth packets to boot users off the legitimate base stations, and catch some of those with our rogue AP who are attempting to reauthenticate with the legitimate base station.
Result
The overall outcome of the first day of testing was not so good, as only 5-6 people were in the office at the time—
Here is what a captured authentication response would look like:
(When someone enters their username and password into the prompt)
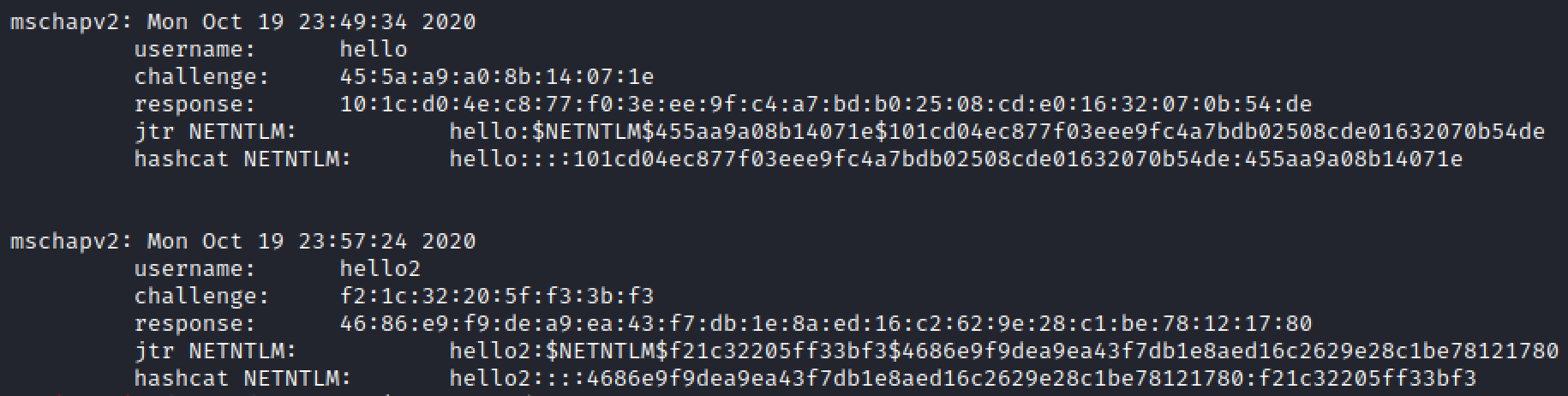
The hashes can then be sent to asleap or hashcat to be cracked offline!
Further attacks
Of course how far this attack can go in terms of depths is determined by how secure/insecure the client network setup is like:
- Do they properly segregate the interal corporate WiFi with the Guest WiFi?
- Do users reuse passwords across both networks? Or their RDP/VPN logins?
- Are there any services running on the internal corporate network that can lead to a foothold scenario? ie. mySQL / FTP / webservers…